For many, the word "registry"still a book with seven seals.
Actually incomprehensible.
Almost everyone has already tampered with the registry with the so-called "tweaking tools".
These tools make changes to the registry, also known as the registry for short,
which is the central configuration database of the operating system.
Here we would like to bring you closer to the function of the registry.
But before we start, one more thing:
This article is not intended for general PC beginners. Moderate experience in using PCs is required. Please only change something in the registry if you know exactly what you are doing! We cannot be held liable for any damage to your PC caused by improper use of the registry. Please remember that deleting or changing a single (incorrect) registry value can irretrievably destroy the operating system!
So before you want to make changes to the registry, you should definitely save them!
Finding your way around the registry
To get into the registry, proceed as follows:
Start-Run
This window opens.
Here you give the command " regedit " a
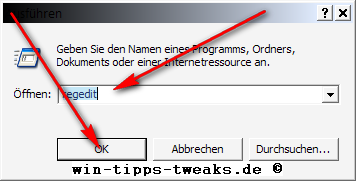
Click on OK and this window appears.
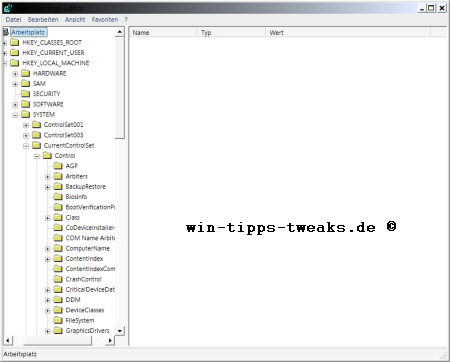
The Registry Editor is basically designed like Explorer and can be used almost the same way. The individual folders are on the left and the corresponding values can be seen in the right window.
The structure of the registry is hierarchical.
It begins in the so-called Haubtschlüsseln (Keys).
Subkeys branch off here.
These always start with "HKEY"
Registry information is made up of several files in the directory Windows \ System32 \ Config together:
- default
- system
- security
- sam
There are also two other files that contain the information of the respective user.
These are the NTUSER. DAT in the register '\Documents and Settings\ of the respective user profile and the file usrClass.dat, which can be found in the respective user profile \Local Settings\Application Data\Microsoft\Windows can be found.
But the " Hive Keys "are composed as follows:
HKEY_CLASSES_ROOT
The information on file extensions is stored here.
These determine, for example, that the correct program is started in Windows Explorer.
HKEY_CURRENT_USER
All configuration information of a currently active user is saved here.
HKEY_USERS
All user profiles and their settings are saved in this key.
HKEY_LOCAL_MACHINE
All system settings of the computer are managed here.
A list of all drivers and hardware of the system is included.
Editing entries:
In order to properly edit (tweak) it is necessary to know how new commands are created.
To do this, a new window must be opened in the corresponding folder with a right-click.
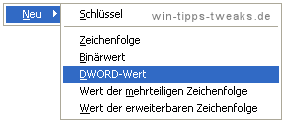
In this a left click on: New
Possible commands are, for example:
DWORD value
These double word files are 32-bit long.
They can be in binary, decimal, or hexadecimal formats.
Binary value
Binary values have no fixed length and can be in binary or hexadecimal format.
string
Texts can be entered here, for example to specify path information or file calls.
Value of the expandable string
An expandable string can contain variables such as % System root% (=Windows directory), which are replaced by their actual value when called.
I hope we were able to give you a little insight into that
Enter registry and thus show that interventions, especially here, can lead to serious errors in the system.
Example
| Transparency: | This article may contain affiliate links. These lead directly to the provider. If a purchase is made through this, we receive a commission. There are no additional costs for you! These links help us to refinance the operation of win-tipps-tweaks.de. |
This tip comes from www.win-tipps-tweaks.de
© Copyright Michael Hille
Warning:
Using Registry Editor or its tips incorrectly can cause serious system problems that may require you to reinstall your operating system. Tampering with the registry files and using the tips is at your own risk.